Sunday, June 8, 2008


Screenshots of Wordcount game
There are two levels in this game.
- Frame the word.
- Find the word.
Frame the word
- You begin the game by choosing either a vowel or a consonant.
- After choosing 9 letters, your count down starts!!!
- Within one minute,you have to form a word using the letters (not necassarily all the letters) in the letter pool.
- Use each letter in the pool only once!
- You score based on the length of your word and maximum length possible.
- 5 times this level is played!
Find the word
- This is simple jumble solving.
- It is a seven letter jumble (with no letter repeating).
- Within 30 seconds you have to solve the jumble.
- If it is correct you score 200 points.
Your final score is out of 700 points.
This is an acid test to your vocabulary skills!
This game is loosely based on the COUNT DOWN game which runs on channel 4 in UK.
Download link: http://kctcse.googlepages.com/WORDCOUNT.ZIP
Labels: Deepak's Scribble, Programming
Friday, June 6, 2008


Screenshots of the game
The game is pretty simple.
Player has the full range of throws to play, as follows :
- He/she can select one of the three, rock or paper or scissors.
- Rock wins against scissors, loses to paper and stalemates against itself.
- Paper wins against Rock, loses to scissors and stalemates against itself.
- Scissors wins against paper, loses to rock and stalemates against itself.
- You get one point for every win and your opponent gets one point for his/her win!!!
- Final winner is the one who scores the maximum points (set at the start of the game) first!!!
It's between you and the computer!
Download link: http://kctcse.googlepages.com/ROCKPAPERSCISSORS.zip
Try the game give your comments on the game.
I am waiting for your comments.
Labels: Deepak's Scribble, Programming
Thursday, June 5, 2008

Screen shot of the Type Racer - Hack!
I am now really happy! I developed a crack to the type racer application in orkut. I set the speed to 85 words per minute because that would sound more realistic. If the speed goes above 100, the type racer asks image verification (very big CAPTCHA). So this is better. You would definitely love this crack to type racer.
I am happy because I atlast developed an internet oriented application!!!
It is a small 130 kb file!!!
Labels: Deepak's Scribble, Programming
Wednesday, June 4, 2008
The softwares that I developed are:
- Torrent timer
- SD's Alarm Clock
- SDPAD
- Key Catcher
- Toggler
This software was the birth of my need to download torrents. My net plan
allows me unlimited download from 2 AM to 8 AM. So I had to wake up early in
the morning to switch on the net, to stop that, I came with the idea of
torrent timer. If you mention the hours and minutes after which the download
should start, this software will start the download automatically. It can
also be used to any other file/software also. I have added an audio player
with this software and the interface has been developed keeping the end
user’s comfort in mind.
Note:
When a playlist of format “.wpl” is opened a special playlist navigator opens
making the audio player user friendly.
Download link: http://kctcse.googlepages.com/TORRENTTIMER.zip
SD's Alarm Clock:

Screen shot of SD's Alarm Clock
It is a simple alarm clock with the feature of adding a music file as the alarm tone.
While enetering the date and time the correct format has to be maintained, otherwise the clock may not work as you desire.
SDPAD:

Screenshot of SDPAD
SDPAD is the replica of notepad! The additional feature is that you can change the color and fonts with better effect than in notepad!!!
Download link: http://kctcse.googlepages.com/SDPAD.zip
Key Catcher:


Screen Shots of key catcher
Off all the softwares I developed, this is the best one.
You can rename the key catcher as SYSTEM because in task manager, this would sound better!!! This software will store the keys pressed in your system when it is running! It will also store the active windows running in the system once every minute. You can hide the key catcher so that it runs invisibly!
Download link: http://kctcse.googlepages.com/KEYCATCHER.zip
TOGGLER:

Screen shot of toggler
This is the first game I had ever developed using VB(any language for that matter).
It is a simple game.
The goal of the game is to turn all the buttons from [X] to [.]. This is done by clicking. When a button is clicked, its state is toggeled, but so is the state of four buttons around it, so plan carefully!
Download link: http://kctcse.googlepages.com/TOGGLER.zip
You download these softwares, work with them and comment on the softwares.
Labels: Deepak's Scribble, Programming
Friday, May 23, 2008
Post your comments about this video.
Labels: Controversial issues
Sunday, May 4, 2008
Read on......
The 10ft Liger who's still growing....
He looks like something from a prehistoric age or a fantastic creation from Hollywood. But Hercules is very much living flesh and blood - as he proves every time he opens his gigantic mouth to roar. Part lion, part tiger, he is not just a big cat but a huge one, standing 10ft tall on his back legs. Called a liger, in reference to his crossbreed parentage, he is the largest of all the cat species.
On a typical day he will devour 20lb of meat, usually beef or chicken, and is capable of eating 100lb at a single setting. At just three years old, Hercules already weighs half a ton. He is the accidental result of two enormous big cats living close together at the Institute of Greatly Endangered and Rare Species, in Miami , Florida , and already dwarfs both his parents.
"Ligers are not something we planned on having," said institute owner Dr Bhagavan Antle. "We have lions and tigers living together in large enclosures and at first we had no idea how well one of the lion boys was getting along with a tiger girl, then loo and behold we had a liger."
50mph runner... Not only that, but he likes to swim, a feat unheard of among water-fearing lions. In the wild it is virtually impossible for lions and tigers to mate. Not only are they enemies likely to kill one another, but most lions are in Africa and most tigers in Asia . But incredible though he is, Hercules is not unique. Ligers have been bred in captivity, deliberately and accidentally, since shortly before World War II.
Today there are believed to be a handful of ligers around the world and a similar number of tigons, the product of a tiger father and lion mother. Tigons are smaller than ligers and take on more physical characteristics of the tiger.
Look at the pictures of this giant...

Labels: Medical Miracles, News
Sunday, April 20, 2008
I would like to introduce a girl to you!
"Adolescent from India, whom with an increase only in 58 cm,
the smallest girl in the world.
Jyoti Amge,14 years, and shorter than an average two-year-old , weighs only 5 kg."
Labels: Medical Miracles, News
Tuesday, April 8, 2008
Rapidshare is the biggest file encyclopedia on the web. It is ranked among the world’s top 20 most visited sites by Alexa. With 100 gigabit/s of internet connectivity it claims to be one of the biggest and fastest web hosters world wide. Rapidshare allows you to upload any type of file from software, to music videos to audio music, games, ebooks and archives.
Searching Rapidshare Using Google
Though Rapidshare is a totally free service, which doesn’t charge its users for uploading or hosting a file on the web, the anonymity of files is still the biggest issue for Rapidshare users. Users cannot search the big great database directly using any search feature to get the content that they are looking for. Here we take the help of Google’s magnificent search capabilities.
Using Google Hidden Operators
Here is a list of great hidden Google operators which can be efficiently used to search files on rapidshare:
Here is what you need to write in Google to search for multimedia content related to your favorite sports car “Ferrari”
site:rapidshare.com "ferrari"
Like wise to search for music, videos and archives you can use the following code:
Music
+inurl:wmamp3ogg site:rapidshare.de
Videos
+inurl:avimpgwmv site:rapidshare.de
Archives
+inurl:exerarzip site:rapidshare.de
Labels: Internet
Friday, April 4, 2008
1. What programming language is GOOGLE developed in?
2. What is the expansion of YAHOO?
3. What is the expansion of ADIDAS?
4. Expansion of Star as in Star TV Network?
5. What is expansion of "ICICI?"
6. What does "baker's dozen" signify?
7. The 1984-85 season. 2nd ODI between India and Pakistan at Sialkot - India 210/3 with
Vengsarkar 94*. Match abandoned. Why?
8. Who is the only man to have written the National Anthems for two different countries?
9. From what four word expression does the word `goodbye` derive?
10. How was Agnes Gonxha Bojaxhiu better known?
11. Name the only other country to have got independence on Aug 15th other than India?
12. Why was James Bond Associated with the Number 007?
13. Who faced the first ball in the first ever One day match in cricket?
14. Which cricketer played for South Africa before it was banned from international
cricket and later represented Zimbabwe ?
15. The faces of which four Presidents are carved at Mt.Rushmore?
16. Which is the only country that is surrounded from all sides by only one country
(other than Vatican )?
17. Which is the only sport which is not allowed to play left handed?

Wanna check the answers????
HERE ARE THE ANSWERS ........
1. Google is written in Asynchronous java-script and XML, or its acronym Ajax ..
2. Yet Another Hierarchy of Officious Oracle
3. ADIDAS- All Day I Dream About Sports
4. Satellite Television Asian Region
5. Industrial credit and Investments Corporation of India
6. A baker's dozen consists of 13 items - 1 more than the items in a normal dozen
7. That match was abandoned after people heard the news of Indira Gandhi being killed.
8. Rabindranath Tagore who wrote national anthem for two different countries one is Indian
's National anthem and another one is for Bangladesh- (Amar Sonar* *Bangla)
9. Goodbye comes from the ex-pression: 'god be with you'.
10. Agnes Gonxha Bojaxhiu is none other Mother Teresa.
11. South Korea ..
12. Because 007 is the ISD code for Russia (or the USSR , as it was known during the cold war)
13. Geoffrey Boycott
14. John Traicos
15. George Washington, Thomas Jefferson, Theodore Roosevelt, and Abraham Lincoln
16. Lesotho surrounded from all sides by South Africa ..
17. Polo.
Labels: Facts
A little boy went into a drug store, reached for a soda carton and pulled it over to the telephone. He climbed onto the carton so that he could reach the buttons on the phone and proceeded to punch in seven digits (phone numbers).
The store-owner observed and listened to the conversation:
Boy: "Lady, Can you give me the job of cutting your lawn?
Woman: (at the other end of the phone line): "I already have someone to cut my lawn."
Woman: I'm very satisfied with the person who is presently cutting my lawn.
Boy: (with more perseverance) : "Lady, I'll even sweepyour curb and your sidewalk, so on Sunday you willhave the prettiest lawn in all of Palm beach , Florida."
Woman: No, thank you.
With a smile on his face, the little boy replaced the receiver. The store-owner, who was listening to all this, walked over to the boy.
Store Owner: "Son... I like your attitude; I like that positive spirit and would like to offer you a job."
Boy: "No thanks"
Store Owner: But you were really pleading for one.
Boy: No Sir, I was just checking my performance at thejob I already have. I am the one who is working for that lady I was talking to
This is what we call "Self Appraisal" .I had done such self appraisals several times,hope many have done it too.What do you say?
Labels: Deepak's Scribble
Wednesday, April 2, 2008

Question : "What would you like to have ..Fruit juice, Soda, Tea, Chocolate, Milo, or Coffee?"
Answer: "tea please"
Question : " Ceylon tea, Herbal tea, Bush tea, Honey bush tea, Ice tea or green tea ?"
Answer : "Ceylon tea "
Question : "How would you like it ? black or white ?"
Answer: "white"
Question: "Milk, Whitener, or Condensed milk ?"
Answer: "With milk "
Question: "Goat milk, Camel milk or cow milk"
Answer: "With cow milk please.
Question: " Milk from Freeze land cow or Afrikaner cow?"
Answer: " Um, I'll take it black. "
Question: " Would you like it with sweetener, sugar or honey?"
Answer: "With sugar"
Question: " Beet sugar or cane sugar ?"
Answer: "Cane sugar "
Question:" White , brown or yellow sugar ?"
Answer: "Forget about tea just give me a glass of water instead."
Question: "Mineral water or still water ? "
Answer: "Mineral water"
Question: "Flavored or non-flavored ?"
Answer: "I'll rather die of thirst"
Labels: Fun
Sunday, March 30, 2008

This post is about how to lock the folder with maximum security.Once you lock your folder,you can't find it anywhere in your system until you unlock it.
First paste the following code in your notepad
cls
@ECHO OFF
title Folder Locker
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" goto UNLOCK
if NOT EXIST Locker goto MDLOCKER
:CONFIRM
echo Are you sure u want to Lock the folder(Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Locker "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
echo Folder locked
goto End
:UNLOCK
echo Enter password to Unlock folder
set/p "pass=>"
if NOT %pass%==type your password here goto FAIL
attrib -h -s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
ren "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" Locker
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Locker
echo Locker created successfully
goto End
:End
save this as a batch file .
ie., filename.bat
Click the batch file and run it.
A new folder called locker will be created.
Keep the files that you want to be locked inside the locker folder and again open that batch file. It will ask whether to lock yes or no.You press Y .
The locker folder will become hidden. So you have locked the folder!!!
Now to open it right click the batch file and select the Edit option and see for these wordings
"if NOT %pass%==type your password here goto FAIL"
alter this as
" if NOT %pass%==((your password)) goto FAIL"
Then you can again get the folder visible!!!
Labels: Windows corner...
Thursday, March 27, 2008
Follow these steps to hide disk drives...
1.Open Registry and navigate to "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\policies\Explorer".
2.Create a new entry by clicking on edit-> new->"Dword value". Name the value as 3fffffff.Now each drive letter has a number.
3.The value of the key will be the sum of the drive letter numbers. Some of the numbers are :
A:=1, B:=2,C:\4,D:=8,e:=16,f:=32,g:=64,H:=128,I:=256,j:=512,k:=1024,L:=2048 and so on. .....
4.Now if you want to hide "C:" and "D:" , you just have to enter value as '12'(4+8). Enter as decimal value in the dword key and restart windows.
5.To get back your drives just delete the key called "3fffffff".
Aeticle idea:http://www.computerlords.blogspot.com/
Labels: Windows corner...
Sunday, March 23, 2008
I had previously posted on ambigrams.This post contains two ambigrams which I missed out on my previous post.
Do you see human face or some other word?
Is this Chinese language???
See the image after 90 degree rotation!
Labels: Attractive Ambigrams, Fun with english
Friday, March 21, 2008
This video was suggested to me by my friend Arun Kumaar.An excellent video of 26 seconds.You will definitely enjoy watching it.
Labels: Fun
Google has included invisible mode feature in GMail Chat last month(Feb 22, 2008). This feature allows you to appear offline and still chat with your friends unlike MSN Messenger. I feel that this is one of the best feature in Yahoo Messenger which is now made available to us in GMail Chat. Please note that this feature is not availble on GTalk Clients. Check out GMail’s Official Blog for more information.
Hope this invisible status is reaches gtalk soon.
Labels: GMail Tricks, GOOGLE, Gtalk
Thursday, March 20, 2008

The regular chess rules are used, although the shape of the board is obviously different.

This is an empty board. Every player has 16 standard chess pieces.

The pawn moves as usual straight forward and takes enemy pieces one square diagonally forward.
The rook moves as always. Nothing new.
The knight is also no different from a standard knight.
Nothing new for the queen as well.
One peculiar feature: the diagonal in the center of the board.

General rules:
Labels: Chess
Tuesday, March 18, 2008
Now the solution for your problem is given below.....
Step 1:Copy the Address of your desired folder from address bar for example if it is C:\FAV copy it(its location on ur hard drive)
Step 2:Goto C:\ drive,goto Tools-->Folder Option-->View-->Hidden Files and Folders-->Hide protected operating system files(Recommended)-->Unhide Hide protected operating system files(Recommended)
#It will give a warning,don't worry!!!
Step 3:Goto C:\Documents and Settings\Administrator\SendTo
#In place of Administrator its your User name
Step 4:Right Click --> New--> Shortcut.Paste The name of your desired folder in "Type the location of the Item" Text Field for Example C:\Fav -->Next-->Finish
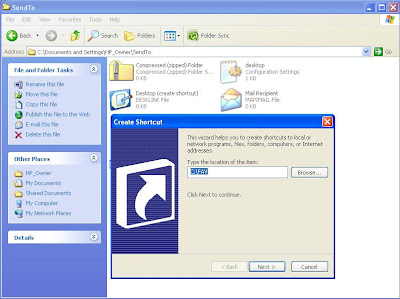
Step 5:Goto C:\ drive,goto Tools-->Folder Option-->View-->Hidden Files and Folders-->Hide protected operating system files(Recommended)-->Hide Hide protected operating system files(Recommended)
#Step 5 is optional
You may browse ur desired folder also.....
Article idea:http://www.computerlords.blogspot.com/
Labels: Windows corner...
Medical Science Report says: When the mother of this chid was pregnant, she had 2 foetuses inside her, but one of the foetus grew inside the other, this is why this girl was born with the other foetus inside her womb.


Labels: Medical Miracles, News
Sunday, March 16, 2008

Having read Dan Brown’s work of DaVinci Code I got interested in reading Digital Fortress, especially knowing that it’s background theme is computers and cryptography. In DaVinci Code, most of the facts look to me like they are accurate, perhaps because I’m not an expert in any of the fields they touch (neither art, fossils or the Vatican situation). But I know something more about computers and I have always liked cryptography, and having read the book,I wanted to know whether the things mentioned in the book is true, I found some things which don’t really fit.
Plot summary(taken from wikipedia)
Susan Fletcher, a brilliant mathematician and head of the National Security Agency's (NSA's) cryptography division, finds herself faced with an unbreakable code named "Digital Fortress", which is resistant to brute-force attacks by the NSA's 3 million processor supercomputer dubbed "TRANSLTR". The code is written by Japanese cryptographer Ensei Tankado, a fired employee of the NSA, who is displeased with the agency's intrusion into people's privacy.
Tankado auctions the algorithm on his website, threatening that his accomplice "North Dakota" will release the algorithm for free if he dies. Tankado is found dead in Seville, Spain. Fletcher, along with her fiancé, David Becker, a skilled linguist and a Professor, must find a solution to stop the spread of the code.
The plot looks really fine,but the informations in this book are not really fine.Some of these things are what we could call “artistic licenses”, where the author has invented something which doesn’t really exist so the novel is interesting, but others are factual errors which look like Dan didn’t get really documented about it. And it’s a pity, because he says two ex-NSA cryptographers contributed to the book and they should know much better what they were talking about.
WARNING: For those who haven’t read the book and have the intention of doing it, this contains all kind of spoilers.
“The notion of a rotating cleartext function was first put forth in an obscure, 1987 paper by a Hungarian mathematician, Josef Harne. Because brute-force computers broke codes by examining cleartext for identifiable word patterns, Harne proposed an encryption algorithm that, in addition to encrypting, shifted decrypted cleartext over a time variant. In theory, the perpetual mutation would ensure that the attacking computer would never locate recognisable word patterns and thus never know when it had found the proper key. The concept was somewhat like the idea of colonising Mars—fathomable on an intellectual level, but, at present, well beyond human ability.”
Although the mentioned mathematician didn’t really exist we could try to believe in the concept of rotating-cleartext but this doesn’t stand. So, an algorithm which produces data that variates over the time so you can’t know whether you got the real data or not. OK, then how does the intended receiver know the data? He will need something more (taking in consideration that this could really work), like the time when it was encrypted and the current time. These will be simply more bits in the keyspace to be brute-forced, so you can always find the original content.
Susan had learned about the Bergofsky Principle early in her career. It was a cornerstone of brute-force technology. It was also Strathmore’s inspiration for building TRANSLTR. The principle clearly stated that if a computer tried enough keys, it was mathematically guaranteed to find the right one. A code’s security was not that its pass-key was unfindable but rather that most people didn’t have the time or equipment to try.”
OK,I never knew there was one such principle, (maybe another invented name). It seems nobody has ever heard about Bergofsky Principle outside this book and for a reason(I spent lot of time in searching about it). It says “mathematically guaranteed to find the right one”, but it would be only correct if it said “mathematically guaranteed to test the right one”.
That is the concept behind brute-force: try all the possible keys, so it’s sure one of them will be the correct one. The difficult part is how to know if the one we tested was the correct one. But, let’s talk about One-time pad, an encryption algorithm “which has been proven, from theoretical first principles, to be unbreakable when properly deployed”.
It works because the key-length is the same as the length of the data, so a lot of different keys will give results which might look like plausible. From a message encrypted with this algorithm you can find the original text you want simply by variating the key used. So, when trying to decode one of this messages TRANSLTR is guaranteed to test the correct key, what is not guaranteed is to be able to know it’s the correct one.
“Susan had created, in effect, a directional beacon disguised as a piece of E-mail. She could send it to the user’s phony address, and the remailing company, performing the duty for which it had been contracted, would forward it to the user’s real address. Once there, the program would record its Internet location and send word back to the NSA. Then the program would disintegrate without a trace. From that day on, as far as the NSA was concerned, anonymous remailers were nothing more than a minor annoyance.”
There’s no way the tracer can work with the current state of e-mail. E-mail is just data, not executable, so the user is the one who has to execute it, it can’t execute itself to know where it is and even less make itself disappear. The only way something like this can work is with web bugs, attaching a link to the email which will be visited when the recipient receives the email and opens it, but it needs the cooperation of the recipient and can’t delete itself (well, maybe if there’s a bug in the e-mail software used to open it, highly doubtable) .
“She knew mutation strings were programming sequences that corrupted data in extremely complex ways. They were very common in computer viruses, particularly viruses that altered large blocks of data.”
This really doesn’t make any sense, so I’m considering it simply another artistic license. Even Dan himself doesn’t seem to know what he wants to represent with mutation strings, so even less do I.
“After we make the switch,” Strathmore added, “I don’t care how many pass-keys are floating around; the more the merrier.” He motioned for her to continue searching. “But until then, we’re playing beat-the-clock.”
So Strathmore’s intention is to replace the file with Digital Fortress code with an altered version of it with a backdoor so the NSA can read all messages encrypted with it. But, what if someone downloaded it previously? He will be able to get the original version without any backdoor, so the plan completely fails. Even more, he can get also the other version with the backdoor, so he will be able to compare both and find the backdoor in it.
“Now Susan was even more doubtful. Encryption algorithms were just mathematical formulas, recipes for scrambling text into code. Mathematicians and programmers created new algorithms every day. There were hundreds of them on the market—PGP, Diffie-Hellman, ZIP, IDEA, El Gamal. TRANSLTR broke all of their codes every day, no problem. To TRANSLTR all codes looked identical, regardless of which algorithm wrote them.”
When he says scrambling text into code I hope he’s not meaning executable code. But, what I don’t like about this paragraph is that he confuses different kinds of algorithms: public-key (El Gamal) and private-key (IDEA), with encryption systems, like PGP which uses the other two in combination to work. PGP is not an algorithm and neither is ZIP, this is a compression system, which can, optionally, encrypt the data, originally with a propietary protocol and nowadays using AES, an standard for encryption. (I searched for these stuffs in wikipedia and google).
““I don’t understand,” she argued. “We’re not talking about reverse-engineering some complex function, we’re talking brute force. PGP, Lucifer, DSA—it doesn’t matter. The algorithm generates a key it thinks is secure, and TRANSLTR keeps guessing until it finds it.””
Susan says the TRANSLTR can find the key even if it doesn’t know what algorithm was used. This is impossible, as you need the algorithm to test whether the key works or not. “Four-bit alpha groupings,” she puzzled. “They’re definitely not part of the programming.”
PFEE SESN RETM MFHA IRWE OOIG MEEN NRMAENET SHAS DCNS IIAA IEER BRNK FBLE LODI
Sorry, Dan, but a bit is either 0 or 1, so these are not four-bit alpha groupings. These are simply 4-character groups, where each character (if using standard codification) uses 8 bits.
“Primes were the fundamental building blocks of all encryption algorithms”
Sorry, but no. There are a lot of encryption algorithms which don’t use prime numbers as its basis, and to put it easy I’ll repeat myself in the example: “one-time pad”.
“Public-key encryption was a concept as simple as it was brilliant. […] The only way to unscramble the message was to enter the sender’s “pass-key”—a secret series of characters that functioned much like a PIN number at an automatic teller.”
Sorry, but again: NO!. this is not how public-key encryption works. If it was better explained it would be how private-key encryption works. But Dan, you need to read the Wikipedia and not say this kind of things.
“With a few quick keystrokes, she pulled up a program called ScreenLock. It was a privacy utility. Every terminal in Node 3 was equipped with it. Because the terminals stayed on around the clock, ScreenLock enabled cryptographers to leave their stations and know that nobody would tamper with their files. Susan entered her five-character privacy code, and her screen went black. It would remain that way until she returned and typed the proper sequence.”
Five character passwords in a computer managed by a NSA member? Not long enough to be credible. The most paranoid of my friends use twenty characters passwords, so I imagine NSA should use something a bit longer than 5 chars. (I myself use 10 character passwords mostly...)
Oh, and Greg manages to install a keylogger in all these computers, so I should say the system operator is not very efficient in keeping the systems secure. At least, lock the computer case inside a box so nobody can access it directly.
To finish this list, how did they plan to decipher the Digital Fortress code if they didn’t have the decryption code? OK, you get the passkey but you need the decryption code, which is encrypted with itself. Mmmm, a no-no…
Let’s get with the errors not related to computers.
In one chapter the assassin Hulohot transmits the message "SUBJECT: P. CLOUCHARDE - TERMINATED", but in another chapter the list of messages reads "SUBJECT: PIERRE CLOUCHARDE - TERMINATED". I am not sure whether this error appears in other editions of the book.(It appeared in my edition).In wikipedia it is said that the information about Seville,Spain were wrong.(I am not too sure about it)
Inspite of all this, I should say I did enjoy reading this wonderful book as much as the DavinCi Code from Dan Brown. His success lies in his art of mixing truth with fiction and making you believe that the fiction was true.If you are not an expert in cryptography then this book is definitely worth a read.
Labels: Book Review

























